Self-Sovereign Identity Platform
Private • Secure • Sovereign • Compliant
kryptooS establishes a new paradigm for digital identity through self-sovereign identifiers and zero-knowledge proofs, ensuring privacy and compliance in a decentralized world.
Pioneering Self-Sovereign Identity solutions
kryptooS focuses on cryptographic foundations that prioritize user privacy while enabling verifiable identity across all digital interactions. Our research combines zero-knowledge proofs with decentralized identifiers to create a sovereign identity ecosystem.
Research deliverables prioritize auditability, composability, and policy alignment for regulated industries.
Developing advanced zero-knowledge proof systems that allow identity verification without revealing personal information. For example, proving you're over 18 without disclosing your birthdate, or verifying employment without sharing salary details.
Building comprehensive DID infrastructure that enables self-sovereign identity across all digital interactions. Users control their identifiers, credentials, and consent mechanisms without relying on centralized authorities.
kryptooS is developing the cryptographic foundations for a privacy-first internet where users truly own and control their digital identities. Our research combines advanced zero-knowledge proofs with decentralized identifier architecture to enable sovereign identity across all applications.
Advanced cryptographic protocols and security frameworks
Privacy-preserving cryptographic proofs enabling identity and compliance verification without exposing sensitive data.
Fully decentralized DID resolution and verification compliant with W3C standards and optimized for cross-chain usage.
Cryptographically verifiable credentials with selective disclosure and enterprise-grade interoperability.
Future-proof cryptographic primitives designed to resist quantum computing attacks while maintaining backward compatibility.
These foundations keep kryptooS secure and interoperable across identity, finance, AI, and governance. The priority is auditability, upgrade-safety, and a practical migration path to post-quantum security.
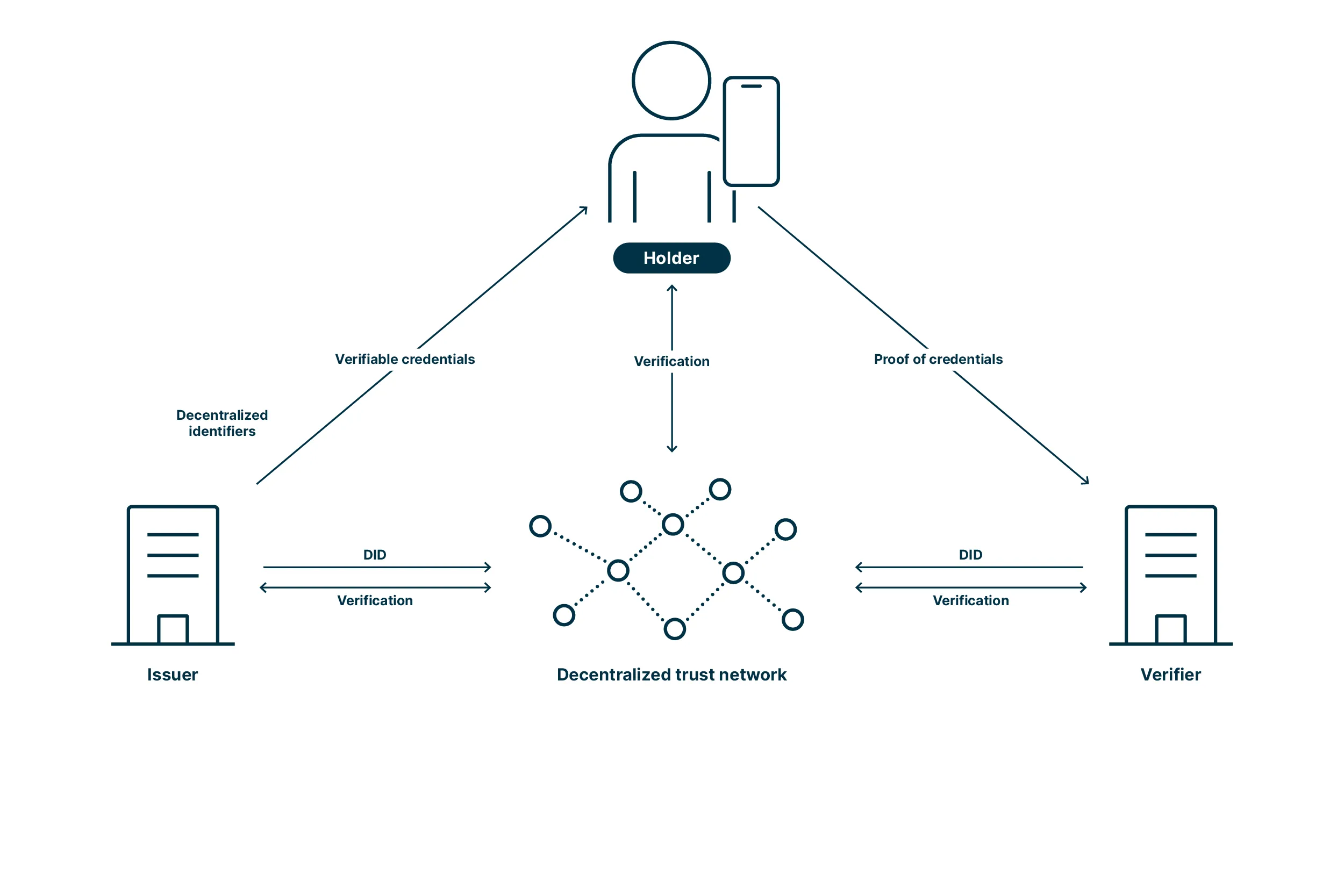
A production-minded SSI architecture: privacy proofs, decentralized identifiers, and compliance claims — designed to be auditable, upgrade-safe, and usable across the Empoorio ecosystem.
Generates and verifies claims (age, sanctions, accreditation) without exposing raw identity attributes.
Resolves DID documents and verification methods across chains with revocation-aware trust.
Privacy-preserving compliance attestations with selective disclosure and minimal retention.
Upgrade-safe primitives with governance-controlled rollout to support post-quantum migration paths.
Implementation is designed to stay practical: measurable security baselines, clear upgrade boundaries, and compatibility paths for regulated deployments.
The stack is built to evolve safely: governance-controlled upgrades, measurable security posture, and migration strategies that avoid breaking identity continuity.
Advanced zero-knowledge and privacy-preserving technologies
This protocol stack is designed for verifiable identity and compliant interactions without building centralized data honeypots.
Self-Sovereign Identity represents a fundamental shift in how we think about digital identity. Users gain complete control over their personal data and digital credentials.
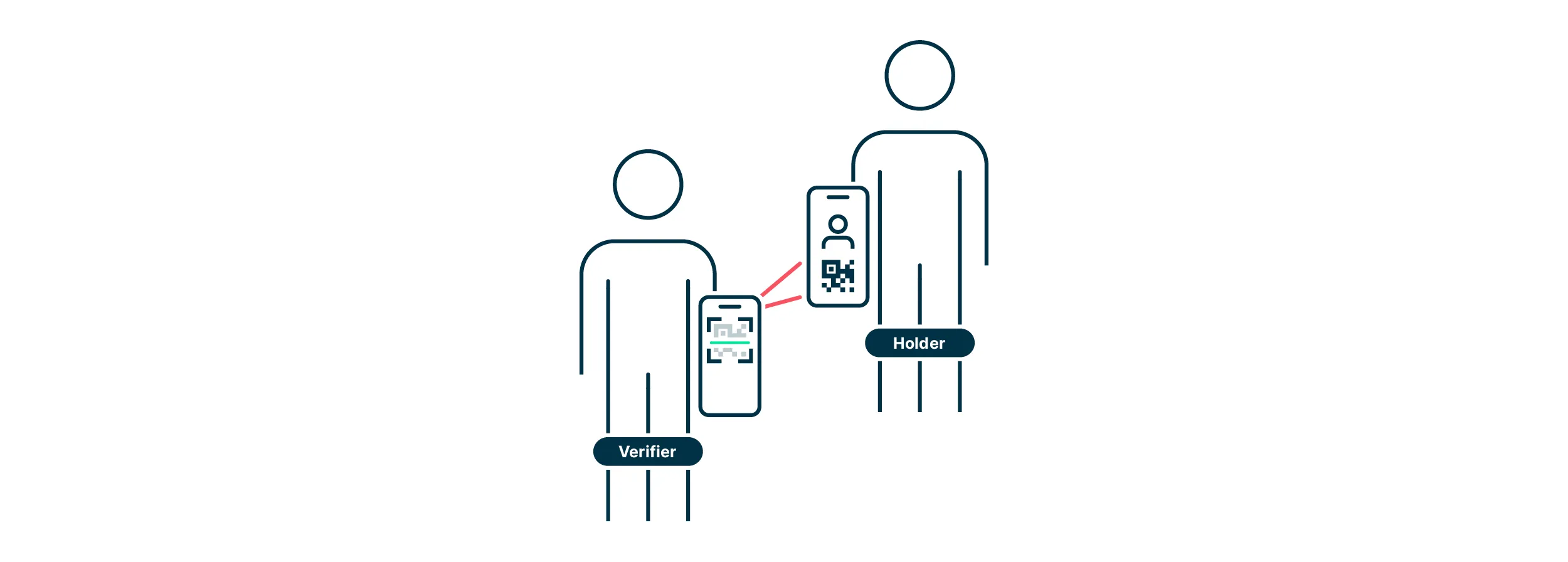
Own and manage your digital identity with decentralized identifiers and verifiable credentials that you control completely.
Share only what you choose to share with zero-knowledge proofs ensuring privacy by design across all interactions.
Works seamlessly across all platforms and services with standards-compliant decentralized identifiers and credentials.
SSI transforms digital identity from centralized control to user sovereignty, enabling privacy-preserving interactions across the entire ecosystem.
How kryptooS integrates across the Empoorio ecosystem
A unified Self-Sovereign Identity layer acting as the cryptographic root of trust for all applications and services within Empoorio.
kryptooS identity propagates across all functional domains without duplicating user data or creating centralized identity silos.
kryptooS acts as the cryptographic backbone of Empoorio, enabling seamless, privacy-preserving identity across blockchain, AI, finance, and user-facing applications.
kryptooS integrates across the full Empoorio stack — from chain-level identity anchoring to wallet custody, AI risk scoring, and dApp authentication.
The integration layer is designed to be composable: apps adopt kryptooS verification and credentials independently, without breaking upgrades or forcing migrations.
Unified identity across the decentralized web
kryptooS will create a unified identity ecosystem where users authenticate across decentralized applications without exposing personal data. Credentials remain portable, revocable, and cryptographically provable.
Prove only what is required (age, residency, accreditation) without revealing raw personal data.
Move identity between Empoorio apps and external platforms with verifiable, standards-aligned credentials.
Instantly invalidate compromised credentials and support secure recovery flows without central custody.
Single sign-on across Empoorio dApps with unified credential management and selective disclosure.
Seamless identity portability between traditional services and decentralized applications.
Privacy-preserving reputation and social connections backed by verifiable credentials.
Prove regulatory requirements with ZK flows and minimal retention, reducing liability and attack surface.